Business Applications
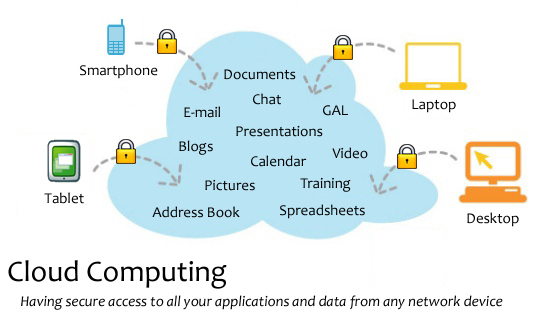
Cloud computing has made businesses more collaborative and easy by incorporating various apps such as MailChimp, Chatter, Google Apps for business, and Quickbooks.
Application Description
1 MailChimp
It offers an e-mail publishing platform. It is widely employed by the businesses to design and send their e-mail campaigns.
2 Chatter
Chatter app helps the employee to share important information about organization in real time. One can get the instant feed regarding any issue.
3 Google
Apps for Business Google offers creating text documents, spreadsheets, presentations, etc., on Google Docswhich allows the business users to share them in collaborating manner.
4 Quickbooks
It offers online accounting solutions for a business. It helps in monitoring cash flow, creating VAT returns and creating business reports.
Data Storage and Backup
Box.com, Mozy, Joukuu are the applications offering data storage and backup services in cloud.Application Description
1 Box.com
Box.com offers drag and drop service for files. It just required to drop the files into Box and access from anywhere.
2 Mozy
Mozy offers online backup service for files during a data loss.
3 Joukuu
Joukuu is a web-based interface. It allows to display a single list of contents for files stored inGoogle Docs, Box.net and Dropbox.
Management Applications
There are apps available for management task such as time tracking, organizing notes. Applications performing such tasks are discussed below:Application Description
1 Toggl
It helps in tracking time period assigned to a particular project.
2 Evernote
Evernote is an application that organizes the sticky notes and even can read the text from images which helps the user to locate the notes easily.
3 Outright
It is an accounting app. It helps to track income, expenses, profits and losses in real time.
Social Applications
There are several social networking services providing websites such as Facebook, Twitter, etc.Application Description
1 Facebook
Facebook offers social networking service. One can share photos, videos, files, status and much more.
2 Twitter
Twitter helps to interact directly with the public. One can follow any celebrity, organization and any person, who is on twitter and can have latest updates regarding the same.
Entertainment Applications
Application Description1 Audiobox.fm
It offers streaming service, i.e., music can be stored online and can be played from cloud using service's own media player.
Art Applications
Application Description1 Moo
It offers art services such as designing and printing business cards, postcards and minicards.